North Korean (DPRK) threat actors are turning to a powerful new blockchain-based method called EtherHiding to steal XRP, Shiba Inu (SHIB), Binance Coin (BNB), and other digital assets.
This is the first time Google Threat Intelligence Group (GTIG) has observed a nation-state actor using this kind of attack to facilitate crypto thefts.
The discovery adds a new layer of concern to the ongoing wave of crypto-targeted hacks, showing how threat actors are evolving to bypass traditional security defenses.
What is EtherHiding?
EtherHiding is a stealthy new approach that uses public blockchains as a resilient command-and-control (C2) layer for malware. The technique was first spotted in September 2023 as part of the CLEARFAKE campaign tracked as UNC5142).
It embeds malicious JavaScript payloads into smart contracts on public blockchains chains like BNB Smart Chain, XRP Ledger and Ethereum.
This allows attackers to host malicious code on a decentralized ledger, a code that’s hard to take down and easy to call from a victim’s browser.
Unlike normal malware that depends on centralized infrastructure, EtherHiding leverages decentralized networks. This makes it nearly impossible for law enforcement to detect.
Moreover, the attackers can update the malicious code at any time, maintaining continuous access to infected systems.
How EtherHiding Works
Below is a simple, step-by-step view of how EtherHiding attacks typically unfold, according to the GTIG report:
Step 1: Initial compromise via social engineering or site breaches
Attackers usually open the door through social engineering like fake job interviews, fraudulent crypto-games, or recruitment lures that target developers.
In some CLEARFAKE cases, the criminals first compromise a legitimate website (often WordPress) using stolen credentials or software flaws. That hacked site becomes the delivery platform.
Step 2: A loader script is injected into the compromised site
The attacker plants a small “loader” JavaScript snippet on the breached site. When a visitor loads the page, this loader runs in the browser and is responsible for reaching out to the blockchain to fetch the real malicious code.
Step 3: The loader fetches payloads from smart contracts using read-only calls
Rather than sending on-chain transactions, the loader performs a read-only call (for example, eth_call) to a smart contract where the attacker has hidden the JavaScript payload.
Because read-only calls don’t write to the ledger, they leave little trace and avoid gas fees, making the fetch quiet and cheap for the attacker.
Step 4: Payload executes and attackers move in
Once the loader downloads the payload, it runs in the victim’s environment. The delivered code can do many things: show fake login or browser-update overlays to steal credentials, install info-stealing malware, or drop persistent backdoors.
In the CLEARFAKE campaign, these stages supported multi-platform infections that targeted Windows, macOS, and Linux systems.
Read also: 8 Common Crypto Scams and How To Avoid Them
Targeting Crypto Developers Through Fake Jobs
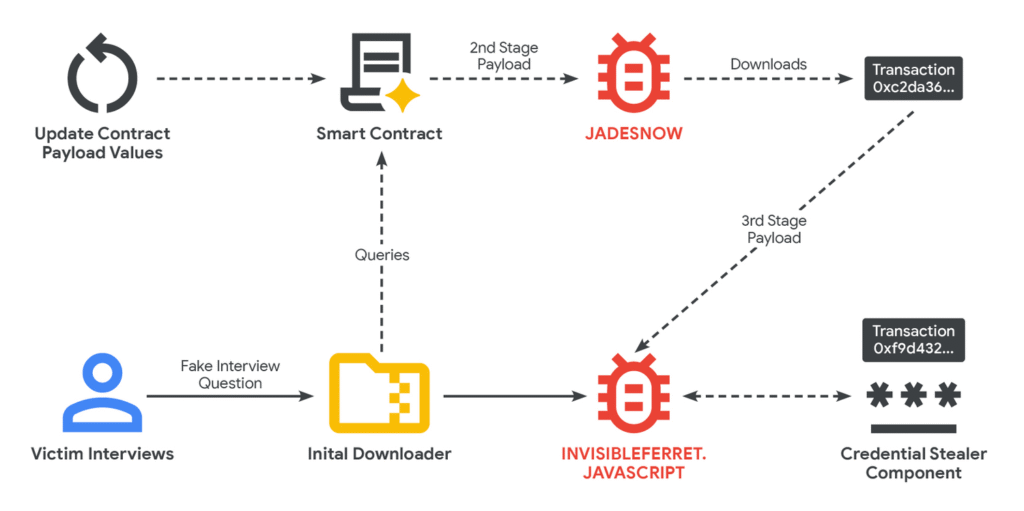
The campaign, dubbed “Contagious Interview,” focuses on developers in the crypto and tech industries.
Hackers pretend to be recruiters from legitimate companies and approach potential victims through Telegram and Discord.
They offer fake job interviews or coding tests, which are actually malware delivery traps. Once the victim downloads and opens the file, their system is compromised, giving hackers access to sensitive information and crypto wallets.
This campaign uses several multi-stage malware variants, including:
- JADESNOW – for initial access and system compromise.
- BEAVERTAIL – for persistence and information stealing.
- INVISIBLEFERRET – for deeper network infiltration.
These malware strains are capable of infecting Windows, macOS, and Linux systems, allowing attackers to maintain long-term control of networks and steal stored crypto assets.
A New Cybersecurity Challenge
According to the report, EtherHiding represents a “next-generation bulletproof hosting” model. In essence, hackers avoid using servers that authorities can shut down by storing malicious code in smart contracts.
The attack uses read-only functions on the blockchain, which means no actual transactions are recorded on the ledger. This helps them stay under the radar and avoid detection.
Related: What is Cryptojacking? How You Can Protect Yourself
How You Can Protect Yourself
Security experts warn that social engineering is a major entry point for these kinds of attacks. Here are practical steps to reduce risk:
- Verify recruiters and company domains before any job interview.
- Avoid downloading coding tests or software from unverified links.
- Use strong endpoint protection and keep devices updated.
- Enable multi-factor authentication on wallets and accounts.
- Monitor wallet activity regularly for suspicious behavior.
The EtherHiding campaign is a stark reminder of how blockchain technology can be used for both good and bad. By blending advanced malware with decentralized infrastructure, North Korean hackers are raising the stakes in the fight against crypto theft.
For crypto holders, developers, and anyone in the digital asset ecosystem, staying vigilant against fake recruiters and malicious links has never been more critical.






